Risk Register Excel template for your risk register Risk Standards PPT overview of the major risk standards A Sample Job Description A detailed sample job description for an ISM ISO 27001 Spreadsheet for scoring the effectiveness of the specified controls Categories Explains and suggests risk. Subject: Re: ISO 27001 security Risk Register To post a message to ISO27k Forum, send an email to iso2700.@googlegroups.com or post online through groups.google.com For more information about ISO27k, visit www.iso27001security.com.
Risk assessment is without a doubt the most fundamental, and sometimes complicated, stage of ISO 27001. Getting the risk assessment right will enable correct identification of risks, which in turn will lead to effective risk management/treatment and ultimately to a working, efficient information security management system. So, which risk assessment methodology is right for ISO 27001? Do you have to use a specific methodology? Do you have to utilize other risk management standards such as ISO 27005, or are you free to choose whichever methodology is best? We explore these questions and more in this article.
As mentioned above, risk assessment is an imperative, key stage of establishing an effective information security
management system. Identifying and treating risks is the fundamental concept of an information security management system – and all ISO 27001 certified information security management systems must have a working risk identification and treatment process in order to be successful. With this in mind, let's explore the core requirements of a risk assessment methodology.
1. Consistent, repeatable, comparable results
The risk assessment methodology must be a consistent, repeatable process that produces comparable results over time. The reason for this is to ensure that risks are identified using consistent criteria, and that results do not vary dramatically over time. Using a methodology that is not consistent i.e. produces widely varied results time after time, does not provide an accurate representation of risks to the business and cannot be relied on. Remember the reason you are performing risk assessments, it is not to satisfy the auditor it is to identify risks to your business and mitigate these. If the results of this process are not useful, there is no point in doing it!
2. Planned Intervals
Risk assessments must be performed at planned intervals, or when significant changes to the business or environment occur. It is usually good practice to set a planned interval e.g. annually to conduct an ISMS-wide risk assessment, with criteria for performing these documented and understood. If there are major changes to the environment i.e. network re-design, moving premises, on-boarding new departments, changes to risk appetite etc. then a risk assessment should be conducted to quantify the risks that these changes may have on the business.
3. Document, Document, Document
The risk assessment methodology should be available as documented information, and should contain or be supported by a working procedure to explain the process. This ensures that any personnel assigned to conduct or review the risk assessment are aware of how the methodology works, and can familiarize themselves with the process. As well as documenting the methodology and procedure, results of the risk assessment must be available as documented information. As well as demonstrating to auditors and internal/external stakeholders that risk assessments have been conducted, this also enables the organisation to review, track and manage risks identified at any point in time. It is usual for risks of a certain criteria to be contained on a risk register, and reviewed as part of risk management meetings. If you are going for ISO 27001 certification, you should be documenting everything you have to provide subjective evidence to auditor.
4. Which risk assessment methodology for ISO 27001?
Iso 27001 Controls
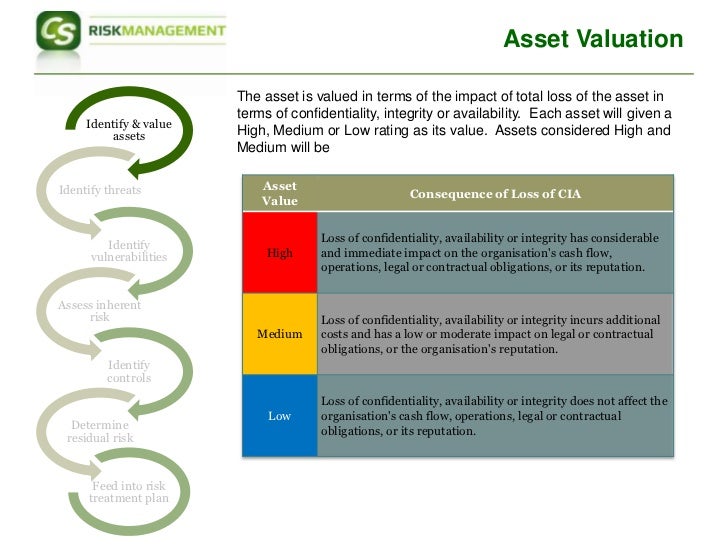
Under ISO 27001:2005, it was a requirement that risk assessment methodologies must use an asset-based approach. This means that the organisation must identify its assets and assess risks against these assets. For example, identifying the HR database as an asset and identifying risks to the HR database.

While it is no longer a specified requirement in the ISO 27001:2013 version of the standard, it is still recommended that an asset-based approach is taken as this supports other requirements such as asset management. Other approaches can be taken, however, and it shouldn't affect ISO 27001 certification if the approach taken is not an asset-based methodology.
Iso 27001 Risk Management Framework
5. Align with other standards?
Iso 27001 Risk Register Template

Iso 27001 Risk Register
Other standards such as ISO 27005 Information Security Risk Management Standard can be used to align with best
practice. ISO 27005 provides guidelines for information security risk management and is considered good practice as the international standard. While it is recommended to look at best practice, it is not a mandatory requirement so if your methodology does not align with standards such as these it is not a non-compliance.
Summary
Risk assessment is without a doubt the most fundamental, and sometimes complicated, stage of ISO 27001. Getting the risk assessment right will enable correct identification of risks, which in turn will lead to effective risk management/treatment and ultimately to a working, efficient information security management system. So, which risk assessment methodology is right for ISO 27001? Do you have to use a specific methodology? Do you have to utilize other risk management standards such as ISO 27005, or are you free to choose whichever methodology is best? We explore these questions and more in this article.
As mentioned above, risk assessment is an imperative, key stage of establishing an effective information security
management system. Identifying and treating risks is the fundamental concept of an information security management system – and all ISO 27001 certified information security management systems must have a working risk identification and treatment process in order to be successful. With this in mind, let's explore the core requirements of a risk assessment methodology.
1. Consistent, repeatable, comparable results
The risk assessment methodology must be a consistent, repeatable process that produces comparable results over time. The reason for this is to ensure that risks are identified using consistent criteria, and that results do not vary dramatically over time. Using a methodology that is not consistent i.e. produces widely varied results time after time, does not provide an accurate representation of risks to the business and cannot be relied on. Remember the reason you are performing risk assessments, it is not to satisfy the auditor it is to identify risks to your business and mitigate these. If the results of this process are not useful, there is no point in doing it!
2. Planned Intervals
Risk assessments must be performed at planned intervals, or when significant changes to the business or environment occur. It is usually good practice to set a planned interval e.g. annually to conduct an ISMS-wide risk assessment, with criteria for performing these documented and understood. If there are major changes to the environment i.e. network re-design, moving premises, on-boarding new departments, changes to risk appetite etc. then a risk assessment should be conducted to quantify the risks that these changes may have on the business.
3. Document, Document, Document
The risk assessment methodology should be available as documented information, and should contain or be supported by a working procedure to explain the process. This ensures that any personnel assigned to conduct or review the risk assessment are aware of how the methodology works, and can familiarize themselves with the process. As well as documenting the methodology and procedure, results of the risk assessment must be available as documented information. As well as demonstrating to auditors and internal/external stakeholders that risk assessments have been conducted, this also enables the organisation to review, track and manage risks identified at any point in time. It is usual for risks of a certain criteria to be contained on a risk register, and reviewed as part of risk management meetings. If you are going for ISO 27001 certification, you should be documenting everything you have to provide subjective evidence to auditor.
4. Which risk assessment methodology for ISO 27001?
Iso 27001 Controls
Under ISO 27001:2005, it was a requirement that risk assessment methodologies must use an asset-based approach. This means that the organisation must identify its assets and assess risks against these assets. For example, identifying the HR database as an asset and identifying risks to the HR database.
While it is no longer a specified requirement in the ISO 27001:2013 version of the standard, it is still recommended that an asset-based approach is taken as this supports other requirements such as asset management. Other approaches can be taken, however, and it shouldn't affect ISO 27001 certification if the approach taken is not an asset-based methodology.
Iso 27001 Risk Management Framework
5. Align with other standards?
Iso 27001 Risk Register Template
Iso 27001 Risk Register
Other standards such as ISO 27005 Information Security Risk Management Standard can be used to align with best
practice. ISO 27005 provides guidelines for information security risk management and is considered good practice as the international standard. While it is recommended to look at best practice, it is not a mandatory requirement so if your methodology does not align with standards such as these it is not a non-compliance.
Summary
Iso 27001 Audit
To summarize, under ISO 27001:2013 there is not a mandatory risk assessment methodology that must be used. While it is recommended to conduct asset-based risk assessments and align with other best practice standards, it is down to the organisation to determine the methodology which suits them best. Whatever methodology is used, it must produce consistent, repeatable and comparable results. Risk assessments must be conducted at defined intervals, by suitably competent personnel, and the outputs must be acted upon as part of a risk treatment plan. The most important thing to remember with risk assessment is that these are being conducted for the benefit of the business and not to satisfy an auditor. If you keep in your mind that you want to identify risks to the business and treat these, then any methodology (providing it is defined, consistent and repeatable) should be sufficient. As you know your business better than anybody, the outputs of the first risk assessment should prove as a useful yard stick as to whether the methodology is suitable or not, and whether it produces accurate results.
You've partly answered your own question. If the analysis is too deep and too detailed, not only will the risk register be extensive but managing, maintaining and simply using it will be problematic. Significant risks may be 'lost among the weeds'. On top of that, you may be spending too much time and effort on analysis, leaving too little left over for treating the risks - and, by the way, learning more about them since risk treatments don't always work out as they should.
Conversely, if the analysis is too superficial/insufficiently detailed, you will probably miss or at least fail to understand significant risks. Risks may be misinterpreted, ignored, or otherwise mis-characterized. On the upside, less analysis means you'll be able to put more of your resources into treating the risks sooner than if you had waited to 'complete' the analysis [hint: it is never 'complete' in the real world!].
Somewhere between those extremes is a happy medium ... but exactly where that is depends on factors such as the nature and maturity of the business and the people involved in the analysis. For example, an organization just setting out on the road towards ISO27k compliance is well advised to pick out and focus on a few 'obvious' information risks first, get to grips with them and treat them, all while gradually gaining experience and maturing. In time, expanding the depth of analysis may be appropriate, particularly for risks that seem to be 'significant', or where incidents and near misses suggest that the risks are worse than they appear, and perhaps weren't even recognized as such. An organization that is critically dependent on information, especially one facing substantial threats and constraints such as legal and regulatory compliance obligations imposed upon it, is in a different position to ... one that isn't!
Aside from the depth of analysis, there's another equally important factor, namely the breadth or scope of analysis. I often rant about cyber-myopia - the over-emphasis on deliberate attacks against networked IT systems, downplaying or ignoring other risks (e.g. incidents with accidental or natural causes, and incidents affecting other forms of information aside from computer data). Thinking more broadly still, information risks are just one class of risks facing the organization: a mining company, for instance, has to deal with health and safety, engineering, commercial, compliance, financial, environmental and other risks, as well as information risks. That bigger picture varies according to the nature of the business, its industry, its owners and competitors etc. Also, the size and complexity of the organization has an influence: information risk management in a diverse global corporation is bound to be different to, say, a hospital.
Oh and another! The method or process of analysis is yet another variable e.g. subjective versus objective approaches, hybrids and experimental methods. There are governance and assurance aspects to this too.
I'll stop there and give others a chance to get a word in, except for one parting comment: there is lots more advice in various ISO27k and other standards, books, methods, websites, webinars, groups etc.
Kind regards,
Gary
_________________________________________________
Gary Hinson
IsecT Ltd., New Zealand
Passionate about infosec awareness, standards and metrics
_________________________________________________
--
You received this message because you are subscribed to the ISO27k Forum.
To post a message to ISO27k Forum, send an email to iso27001...@googlegroups.com or post online through groups.google.com For more information about ISO27k, visit www.iso27001security.com Please respect the Forum's rules at www.iso27001security.com/html/forum.html#TipsAndEtiquette
---
You received this message because you are subscribed to the Google Groups 'ISO 27001 security' group.
To unsubscribe from this group and stop receiving emails from it, send an email to iso27001...@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/iso27001security/f49b3dd8-70dc-4bd5-b50a-486ed30f8cc7%40googlegroups.com.
For more options, visit https://groups.google.com/d/optout.
